e-Authentication for Business
Is e-Authentication required for my business?
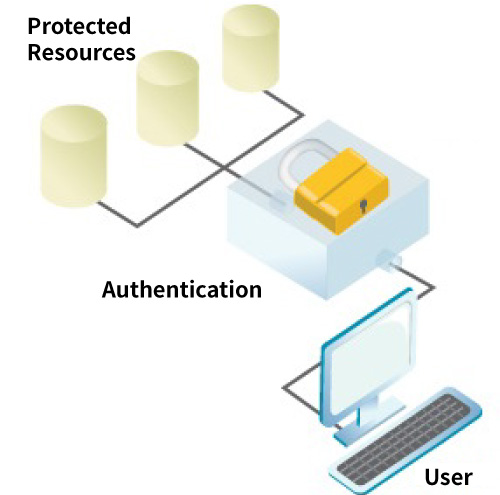
The Internet has revolutionised the mode of delivery of information and services. Provision of online business functions is now a prerequisite for a company to stay competitive. To automate core business processes, businesses have to give their users, including customers, suppliers and employees, access to corporate information and applications anytime / anywhere.
To prevent unauthorised users from gaining access to protected resources, secure authentication systems are required to ensure that users are who they claim to be.
e-Authentication is an important element in the establishment of trust on electronic transactions. Two major processes are involved:
1. Enrolment Process
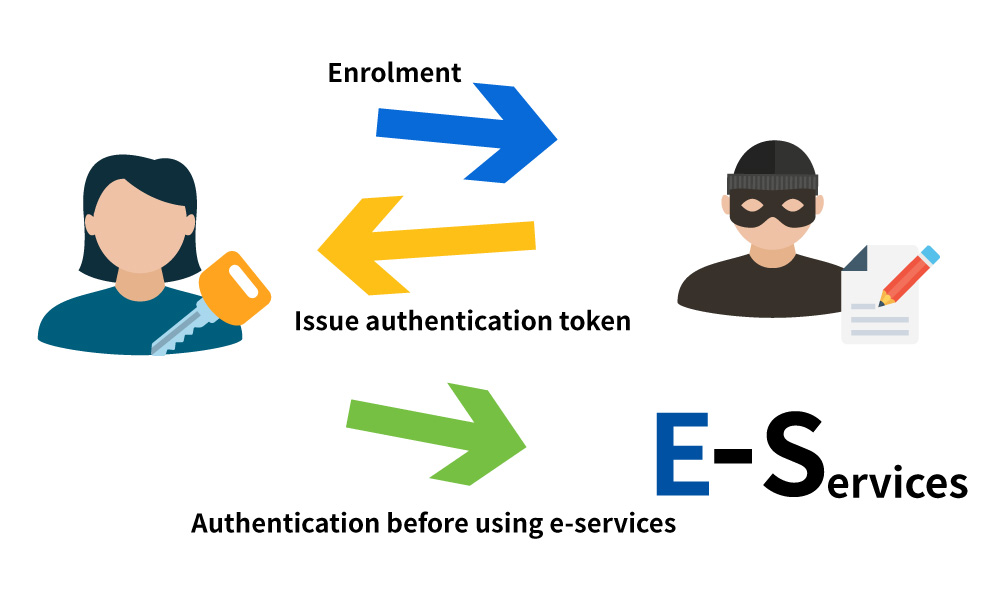
The enrolment process normally consists of two major components, namely Enrolment and Revocation.
Enrolment is
Revocation is
2. Authentication Process
Authentication is the process to identify and prove the identity of a user/party who attempts to send messages or access data. The objective is
Enrolment
Broadly speaking, there are three types of attacks in the enrolment process:
Authentication
There are also four main sources of threats in the authentication process:
Other Sources of Threats
Other than the enrolment and authentication processes, some security attacks may also lead to threats in e-Authentication.
The attacker uses fake email messages that appear to come from a legitimate organisation and asks the victim to provide sensitive information such as account ID, password, etc. or provides a link to a fraudulent website for the victim to enter sensitive information.
The attacker exploits vulnerabilities of computer systems to gain access to and steal information of sensitive personal data, passwords, etc. for further attacks such as impersonation or taking control of accounts.
The hacker installs malicious codes or scripts on a legitimate website such that when the victim visits the site, the malicious scripts will be executed to steal sensitive information or redirect the victim to another fraudulent website with a similar look to the legitimate site.







