What is e-Authentication Assurance Level
The Assurance Level is a term to describe the degree of confidence in the enrolment and authentication processes. The following are their detailed descriptions:
| Level | Definition | Example |
|---|---|---|
 |
Little or no confidence in the claimed or asserted identity. This assurance level is used when minimum risk is associated with erroneous authentication. The authentication mechanism can provide some confidence that the entity is the same over consecutive authentication events. |
Visitors and customers register with a valid email address for receiving promotional newsletters from an online shop. Email addresses may be used for registration without the consent of the respective email users. The users may experience minimal inconvenience arising from the unsolicited confirmation emails. Click here for more details |
 |
Some confidence in the claimed or asserted identity. This assurance level is used when moderate risk is associated with erroneous authentication. |
A package delivery company provides online package tracking services for customers to check the real-time status of shipments, access their billing statements and maintain their accounts. The associated risks are not high if the services do not disclose sensitive information. Click here for more details |
 |
High confidence in the claimed or asserted identity. This assurance level is used where substantial risk is associated with erroneous authentication. |
A cosmetic surgery centre has an online system to allow patients to retrieve their own medical records and the staff to manage the medical records, where improper access to the system could result in the release of sensitive information, thereby causing substantial distress to patients. Click here for more details |

|
Very high confidence in the claimed or asserted identity. This assurance level is used when severe risk is associated with erroneous authentication. |
A law firm uses a system to manage cases, client contacts, billing and other legal documents. Vicious alteration of case records could affect the legal proceedings related to civil or criminal violations. Click here for more details |
e-Authentication Implementation Process Flow
The following is a suggested process flow for businesses to implement a secure e-Authentication system.
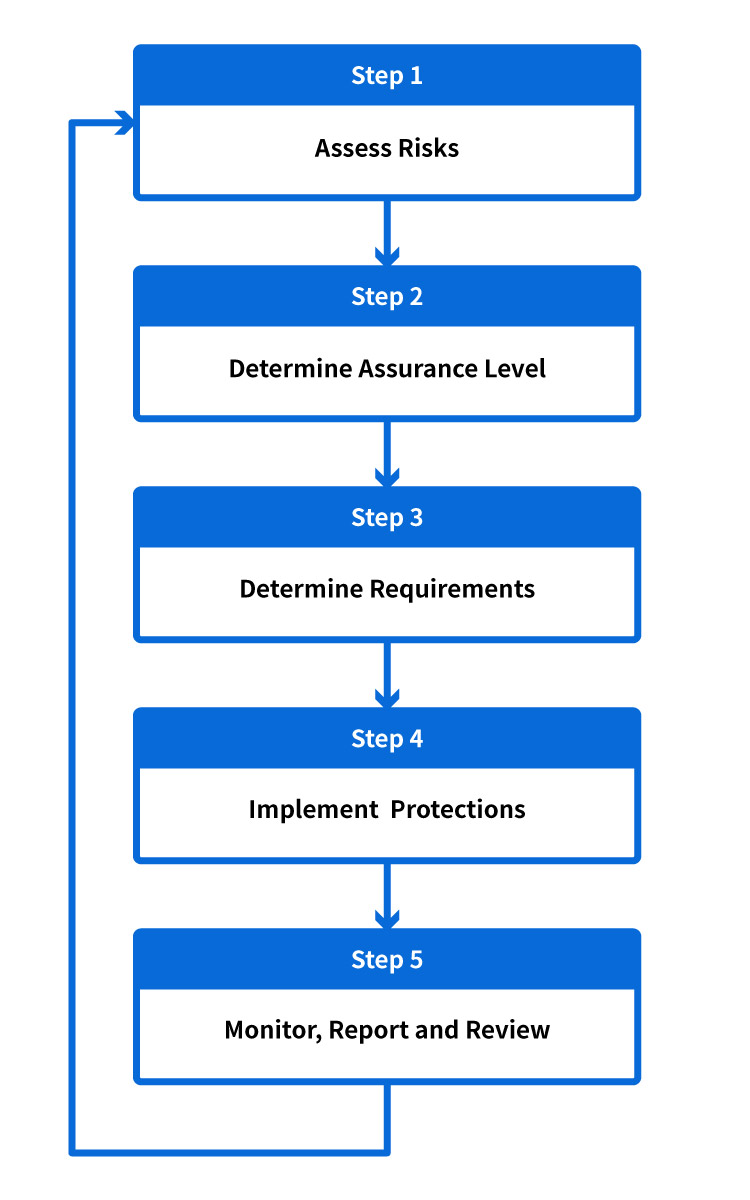
Risk assessment is the first step to identify what authentication methods and security measures are required. Risks can be measured by the likelihood and impacts of an incident and can be financial, including immediate, direct and consequential damages arising from faulty execution or delayed execution. It may also relate to, among other things, loss of confidentiality or privacy, damages to reputation, or identity theft.
Common categories of impacts are listed out below for reference. Additional impacts on specific service nature or business requirements may have to be further identified.
The degree of impact may vary from minimum to severe. The potential degree of impact can generally be grouped as follows:
A reference assessment table that illustrates the maximum impact that can be covered by different assurance levels is listed below. The potential degree of impact identified for a category is associated with an appropriate assurance level that can cover it. The highest assurance level resulting from this mapping exercise will be chosen as the overall assurance level of that particular service or transaction.
Maximum Impact that can be covered
| Potential Impact | Assurance Level 1 | Assurance Level 2 | Assurance Level 3 | Assurance Level 4 |
|---|---|---|---|---|
| Inconvenience, distress, or damage to standing / reputation | N/A / Minimum | Moderate | Substantial | Severe |
| Financial loss or agency liability | N/A / Minimum | Moderate | Substantial | Severe |
| Harm to the organisation or public interests | N/A | Minimum | Moderate / Substantial | Severe |
| Unauthorised release of sensitive information | N/A | Minimum / Moderate | Substantial | Severe |
| Personal safety | N/A | N/A | Minimum / Moderate | Substantial / Severe |
| Civil or criminal violations | N/A | Minimum | Moderate / Substantial | Severe |
For example, if all the ratings of the impact categories were found to be “Minimum”, the service or transaction would require an overall Assurance Level 3. This is because Assurance Level 2 cannot cover even a “Minimum Risk” in the category of “Personal safety”.
The basic requirements (Enrolment and Authentication) for each assurance level are described as follows:
| Level | Enrolment Requirement | Authentication Requirement |
|---|---|---|
 |
Self-claimed or self-asserted identities are accepted without verification. |
No specific requirement for the authentication mechanism used.
Use of cryptographic authentication method not required. |
 |
Identity proof by presentation of identity information issued or approved by at least one policy-compliant authoritative source. |
Single-factor authentication with secure authentication protocol.
|
 |
Verification of identity information with one or more authoritative sources. |
Hard or soft cryptographic authentication tokens with at least two authentication factors are required.
Secret information exchanged in authentication protocols shall be cryptographically protected in transit and at rest. |
 |
In-person verification of identity documents with photos issued by the Government is required in all situations to protect against impersonation. |
Same security measures at Level 3.
Hard tokens with tamper-resistant hardware for storage of secret or cryptographic keys required. |
Based on the determined requirements for the enrolment and authentication processes, the applicable authentication methods and appropriate measures to minimise the associated risks or impacts can then be implemented.
It should be noted that the overall security of an information system would depend on a number of factors. The sole use of a strong authentication token device does not necessarily ensure or improve the security level. There are other mitigation measures that may be deployed in designing a secure information system. The following protection activities are of particular importance:
In addition, each participating party (e.g. user, technical support, user support, management) should understand his/her associated role and responsibility and be accountable for his/her actions.
Mechanisms of constant monitoring and recording are important elements that should be established such that sufficient information can be obtained and proper arrangements can be made when tackling a security incident.
Day-to-day operational data such as audit trail of applications, event history, error log, access records or authorisation data should be properly recorded and backed up to support incident handling or other necessary security procedures.
In addition, the continual review and assessment should form an integral part of the whole system to take into account technological advances and to ensure that proper measures are put in place to cope with new requirements and changes in the underlying environment.
