Identity Management
Identity management (IdM) in an enterprise is a combination of processes and technologies to manage and secure access to the information and resources of an organisation.
IdM describes the core administration and management activities of an identity throughout its life cycle. The activities include provisioning, authentication, authorisation & access control, de-provisioning and audit & review.
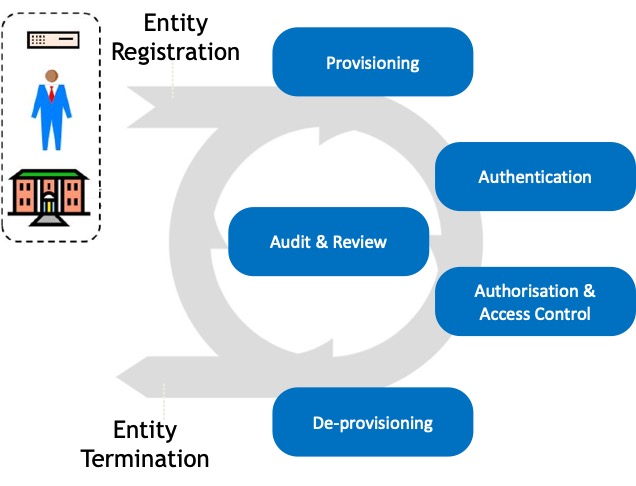
This is the process for the creation of identities of an entity in one or multiple applications/systems/devices based on a set of business rules.
Authentication is the process of gaining confidence in a claimed identity. This is to minimise the threat of identity theft and is comparable to having to present an identity card whenever you use your credit card.
Authorisation & Access Control
Authorisation is the access control process for granting a person or other entity permission to access resources. The access control process has various control levels, e.g. resource level, function level and data level.
The deletion and revocation of identities in IT system(s) based on data from authoritative data sources. This process must be properly recorded for audit purposes. If an identity were improperly deleted and revoked, the Identity Provider (IdP) of the identity would open to potentially significant liabilities.
This includes the generation of audit log records for all administration activities to ensure accountabilities.
IdM facilitates secure access to the information and resources of organisation. It will improve user accountability, strengthen access control, increase system auditability, improve user experience and convenience, enhance effectiveness of user provisioning and improve productivity and administrative efficiency.
IdM Implementation Model
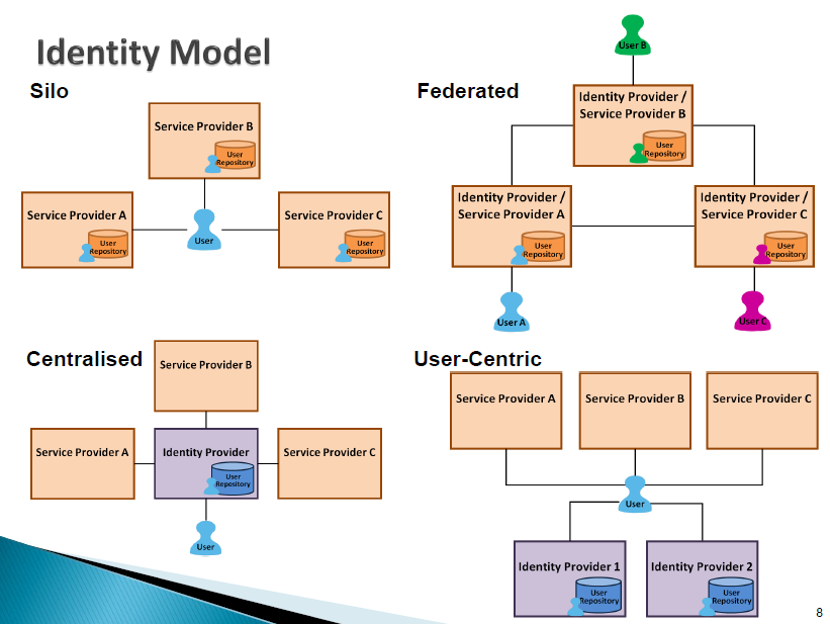
There are four types of IdM Implementation Model.
A “siloed” identity system is designed to operate in a standalone manner and there is no linkage with other identity systems.
With the Centralised model, a person’s identity data is stored independently of the application silos in a repository such as a directory. With this arrangement, the identity data is then made available to services provides (SPs) from a central source.
With the Federated model, SPs do not aggregate and store their account information in a central store, but rather establish a central “IdP” that keeps track of which user identifiers correspond to the same user.
With the User-Centric Model, it enables users to select IdPs independently of SPs and do not need to share their personal information to SPs in order to receive services. In this model, IdPs act as trusted third parties to store user account and profile information and authenticate users, and SPs accept assertions or claims about users from IdPs. Therefore, it gives users greater control over their personal information.
Identity federation benefits users by improving user convenience through single sign-on (SSO) and relieving identity administration workload through reduction in help desk calls.
To achieve interoperability, leading standards bodies, such as OASIS, OpenID Foundation and Liberty Alliance, formulate federation standards and technologies (e.g. SAML) to facilitate the implementation of federated identity management and federated authentication for SSO.
Authentication and Authorisation
Authentication techniques make use of one or more of the following factors:
1.
something you know (e.g. password),
2.
something you have (e.g. a smart card),
3.
something you are (e.g. fingerprint)
If two of these factors are needed for successful authentication, it is termed a “two-factor authentication”. Two-factor authentication is generally believed to be more secure, and therefore many high-risk systems such as Internet banking are now implementing schemes like this.
Authorisation is a process that determines whether an entity is allowed access to a given asset or resource. Common access control models are:
1.
Discretionary Access Control (DAC): in this mechanism, users own the objects under their control, and the granting and revoking of access control privileges are left to the discretion of individual users.
2.
Mandatory Access Control (MAC): it is a means of restricting access to objects based on the sensitivity of the information contained in the objects, along with formal authorisation of subjects to access information of such sensitivity.
3.
Role-based access control (RBAC): it is an authorisation mechanism in which access decisions are based on the roles that individual users have as part of an organisation.
When assigning access rights to an entity, the principles of least privilege and separation of duties are strongly recommended. The principle of least privilege recommends that the least amount of privileges necessary to perform one’s task should be granted to an entity. The principle of segregation of duties suggests that critical functions are divided into steps among different individuals to prevent a single individual from subverting a critical process.


