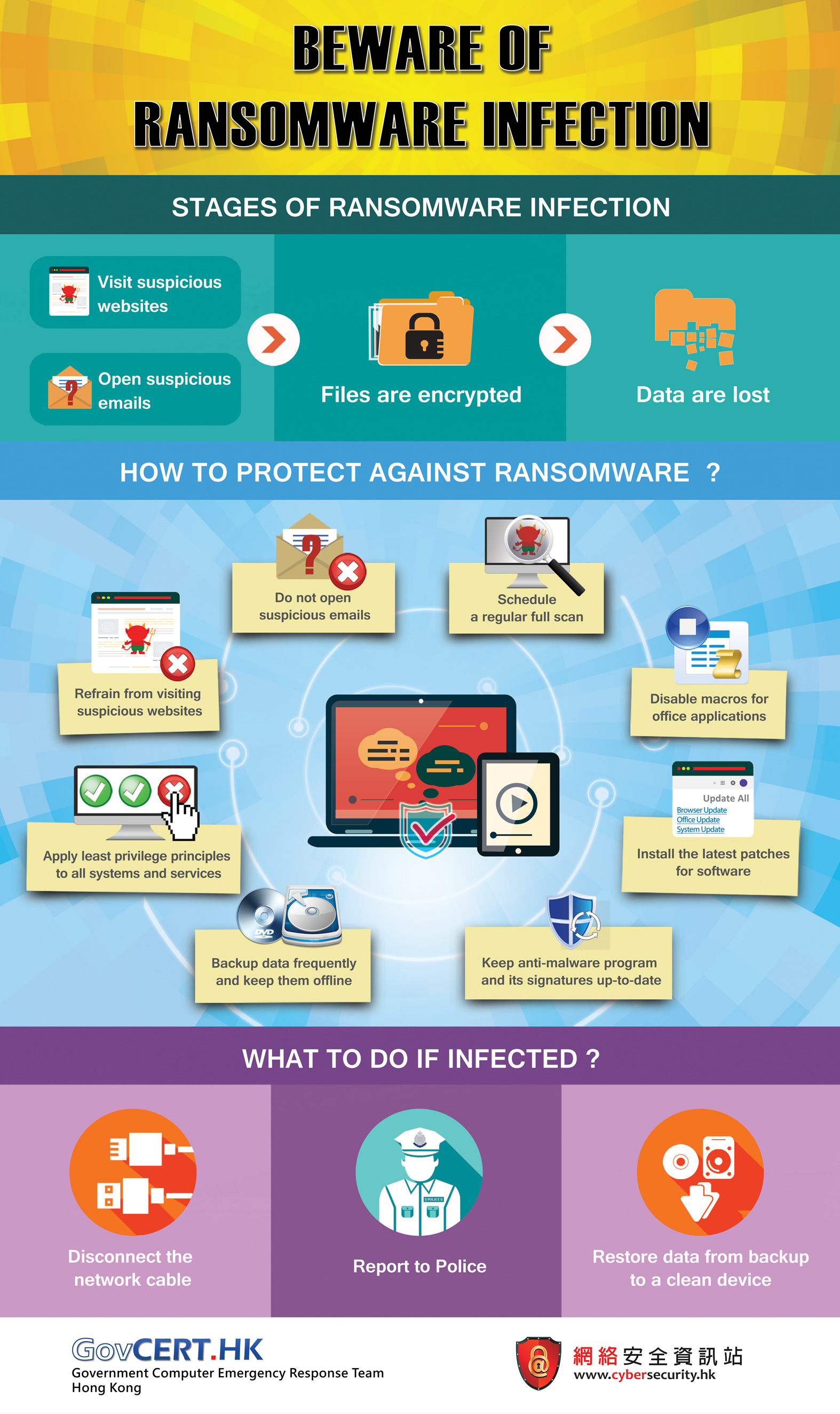
Ransomware
Ransomware is a type of malware that attackers use to blackmail victims by encrypting the data (also known as crypto-ransomware) or simply locking the system rendering the system / data inaccessible to the victims. Tactics adopted by attackers to press the victims to pay the ransoms, usually in the form of cryptocurrency, evolve over time. Some attackers will threaten to make public the stolen information if victims fail to pay up.
Ransomware uses a complex set of evasion techniques which makes it harder for traditional anti-malware software to detect, let alone many businesses which are lacking in visibility tools, IT professionals or other related resources to detect and prevent ransomware. Some ransomware variants can spread and encrypt files that are stored on local drive, network drive, or even cloud storage without the knowledge of the end-user. If a computer or network is infected with ransomware, there are some warning signs requiring special attention such as device’s screen locking, scrambled or encrypted files, disabled anti-malware software and last of all, receiving ransom notice.
According to a global cyber threat report published by a network security company in 2021, the ransomware attack volume in the first six months increased by 151 percent over the same period in 2020 with some 304.7 million attempted attacks logged. Ransomware remains the most prominent threat that the attacks keep evolving and applying different extortion methods for a greater amount of ransom payment.
Recent ransomware attack tactics and trends:
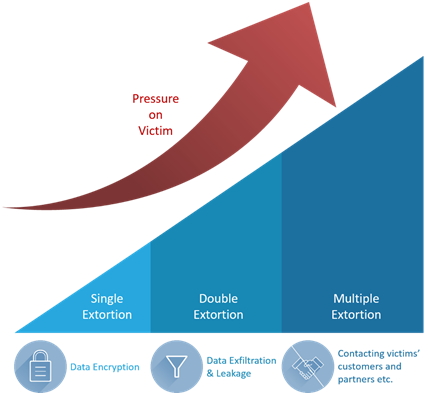
Figure 1: Extortion tactics evolution
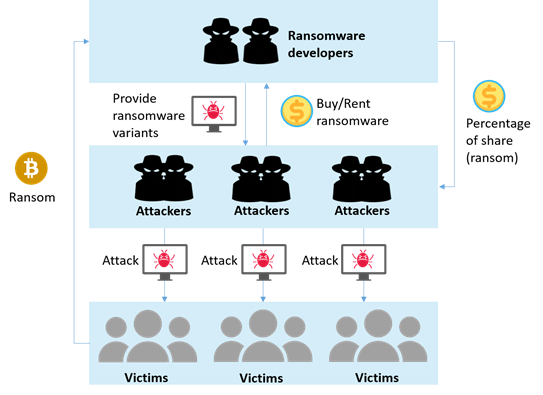
Figure 2: Ransomware-as-a-service (RaaS) workflow
Ransomware will cause adverse impact on an organisation in a variety of ways.
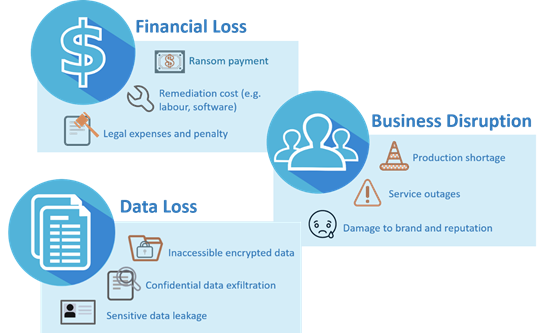
Figure 3: Impact of Ransomware attack
Business revenue will drop and a substantial loss will be incurred as a result of the associated incident response and mitigation efforts made.
Data loss will cause widespread impacts, ranging from disruption to permanent business failure.
The operation of an organisation will be severely affected by the inability to access data and interruption of system processes.
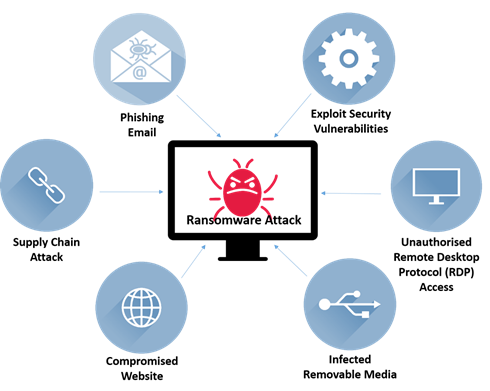
Figure 4: Common ransomware attack vectors
Ransomware is often spread through watering hole phishing or malware-based pharming from a fraudulent website. Once users are deceived into downloading the malicious programs, ransomware can be installed onto users’ computers to initiate ransomware attack without users’ knowledge.
Attackers may use exploit kits to attack vulnerabilities in systems so they can install and launch ransomware attack (e.g. unpatched security vulnerabilities or hidden backdoor programs).
Attackers can access to systems of multiple organisations through trusted third-party vendors. Ransomware attack can be carried out by exploiting interconnected supply chain systems’ vulnerabilities to steal sensitive information, and block access to files by encrypting them.
Attackers can gain access to victims’ network remotely through RDP brute forcing or vulnerable RDP software, install and launch ransomware attack on victims’ system.
Attackers often initiate drive-by attack, taking advantage of known vulnerabilities in the software of legitimate websites. When victims visit the infected website, the ransomware will be downloaded and executed automatically without user’s knowledge.
USB devices and other removable media offer an easy and convenient way to spread ransomware between computers that are not directly connected to each other or to the Internet. Connecting an infected external media can lead to installing and launching attack on local computer and potentially spreading across the network.
The following practices can be adopted to reduce the risk of potential ransomware attacks:
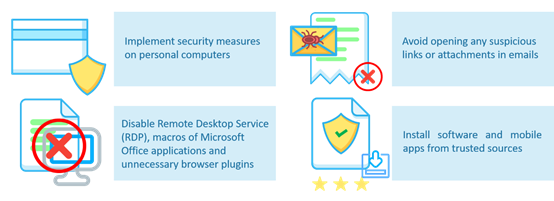
Figure 5: General recommendations for preventing ransomware attack
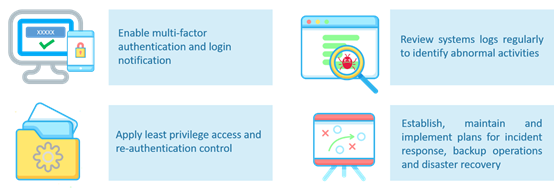
Figure 6: Recommendations for organisations on preventing ransomware attack
It is inadvisable to pay ransoms since there is no guarantee that encrypted data will be successfully recovered, stolen data will be destroyed as promised, infected system will be unlocked and potential attack will be eliminated in the future.
In the event of a ransomware attack, individuals or organisations should consider taking the following actions to effectively respond to and contain the incident:

Figure 7: Response to ransomware attack
Immediate Response
Notify and report
Recovery
Disclaimer: Users are also recommended to observe the disclaimer of this website and read the user agreements and privacy policies of the security software and tools before download and use them.