Supply Chain Attack
Nowadays, cyber attacks and security breaches are very sophisticated and take different forms. Among others, supply chain attacks are becoming increasingly popular since attackers can access systems of multiple organisations through trusted third-party vendors. Even organisations with the most robust data security systems may still be susceptible to cyber attacks or security breaches due to the vulnerabilities of commercial or open source software/system components with malicious codes being injected by attackers.
Supply chain attacks are on the rise and has recorded a rally of 430% increase in 2020. In December 2020, a sophisticated supply chain attack targeted a widely used network management product with multiple vulnerabilities identified. The attacker staged an unprecedented backdoor malware through a legitimate software update that caused over 30 000 organisations including government agencies vulnerable for a couple of months. Supply chain attacks targeting open source software should not be ignored since 90% of applications contain open source codes and 11% of those have known vulnerabilities.
Increasingly interconnected global supply chains make cyber attacks very difficult to mitigate. Cyber attacks can occur at any stage of the supply chain which may lead to:
Attackers can exploit supply chain vulnerabilities through contaminating the software concerned to steal an organisation’s intellectual property information, corrupt trusted software codes, eavesdrop on systems with sensitive data, and carry out further malicious activities. In fact, such attacks often involve the delivery of malware that allow for data harvesting, exfiltration or privilege escalation on targeted systems. Attackers are also able to maintain their presence on targeted networks to perform the aforementioned malicious activities.
Securing the supply chain involves a holistic approach to security, knowing that simply technical solutions can hardly address the breadth of potential threats and vulnerabilities. Organisations should not only examine the vulnerabilities of the software components involved but also consider potential attacks against a physical equipment asset that may be damaged, disabled or used by others for malicious intents.
Supply chain risks may affect the confidentiality, integrity, or availability of systems including unauthorised access to enterprise data, implantation of malicious codes into software and firmware, etc. Attackers could exploit interconnected supply chain systems’ vulnerabilities to trigger remote code execution and sensitive information disclosure as well as re-programming of a device to facilitate other cyber attacks.
Sources of risks include but not limited to:
Supply chains consist of many parties, while most organisations lack the visibility of their data across these relationships, including which parties can access sensitive or proprietary information. Targeted attacks intentionally leverage the digital supply chain to access sensitive data.
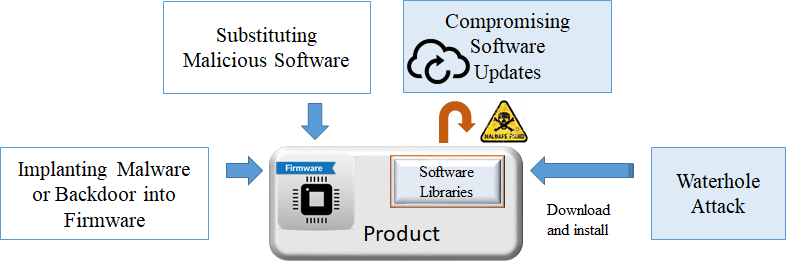
In general, there are three kinds of supply chain attacks: hardware, software and firmware. A hardware supply chain attack requires the physical altering of the microcode of a device, or the addition of another component onto the board that can enable control access or data exfiltration.
A software supply chain attack in particular can target application products at any stage of the development life cycle to achieve unauthorised access and enable sabotage. Attackers can use deception techniques such as disguising malware as legitimate software to access and modify the source code of genuine application programs (e.g. inserting an attack code into the code library by maliciously altered compilers or through the backdoor implanted in the system during development or maintenance). Attackers may also seek to exploit tools and third-party shared software libraries in addition to compromising the infrastructure of developers and distributors.
There are several mitigation measures and best practices that can be adopted to improve an organisation’s security posture and reduce the risk of supply chain infections:
For organisations
For third-party vendors and providers
Disclaimer: Users are also recommended to observe the disclaimer of this website and read the user agreements and privacy policies of the security software and tools before downloading and using them.
