DoS / DDoS Attacks
Denial of service (DoS) and distributed denial of service (DDoS) attacks are among the most common cyber threats on the Internet. The mechanisms behind these attacks are more or less the same and they share the same evil goal of degrading the performance or exhausting resources of the target systems, rendering them unusable or inaccessible. Such targeted systems include websites, email services, Domain Name System (DNS) and web-based applications, etc.
DoS attacks usually involve only a small number of hosts, or even just one host, with an intention to overwhelm the capacity of the target system. If the target system cannot handle the requests sent by the hosts who launched the attack, the availability of the target system will be compromised.
DDoS attacks, on the other hand, are large-scale DoS attacks. The attacker will orchestrate a synchronised DoS attacks to target a specific service / network / server by remotely control a number of compromised hosts. Attackers may adopt common attack techniques like reflective amplification to upscale the attack and cause as much operational disruption as possible. According to a news report, an information technology service provider experienced a DDoS attack on DNS which caused service outage around the globe for several hours in April 2021. Some of the cloud services provided by the service provider became inaccessible. The incident shows that DDoS attacks can significantly affect the service of an organisation which may in turn result in potential loss.
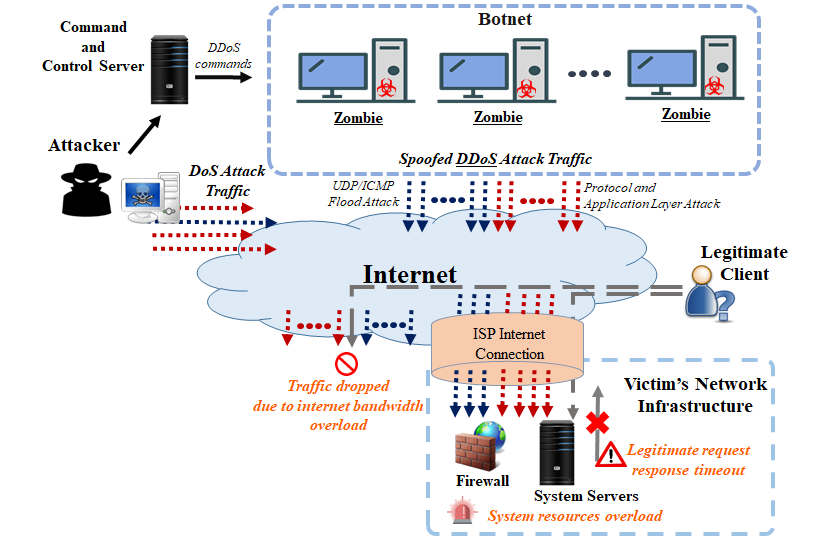
Figure 1: Typical DoS / DDoS Attack Diagram
Moreover, DDoS attacks are sometimes used as a decoy to distract an organisation’s cyber security operations while other malicious activities, such as data theft or network infiltration, are underway.
For simplicity, DDoS is quoted to include DDoS and DoS in the subsequent sections.
The impact of a DDoS incident can be devastating to an organisation from both financial and operational perspectives. The consequences of a DDoS attack may include:
DDoS attacks can be broadly classified into the following four major categories:
Examples: User Datagram Protocol (UDP) floods, Internet Control Message Protocol (ICMP) floods and DNS flood attack
Examples: SYN flood and Secure Sockets Layer (SSL) / Transport Layer Security (TLS) exhaustion
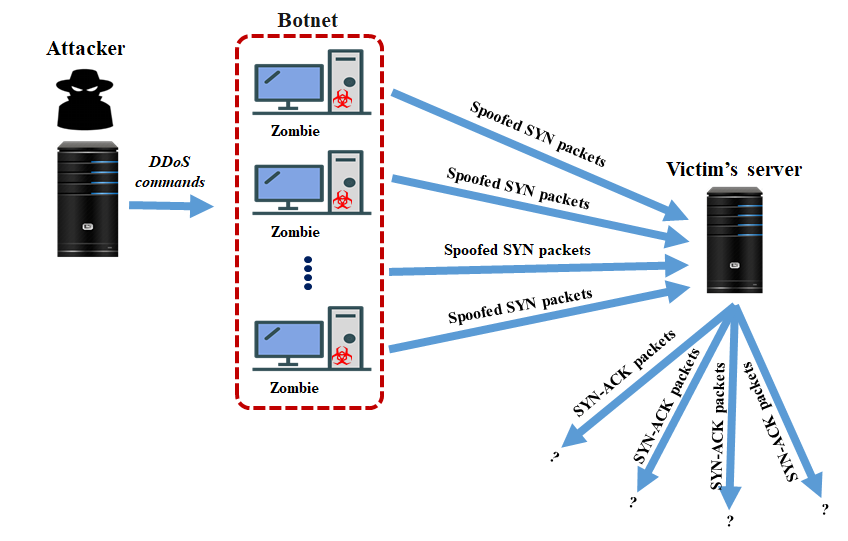
Figure 2: Example of a SYN flood attack
Examples: Slowloris DoS / DDoS attacks, HTTP get / post floods
Examples: Connection-less Lightweight Directory Access Protocol (CLDAP) amplification attacks, DNS amplification attacks, distributed reflective denial of service (DRDoS) attacks
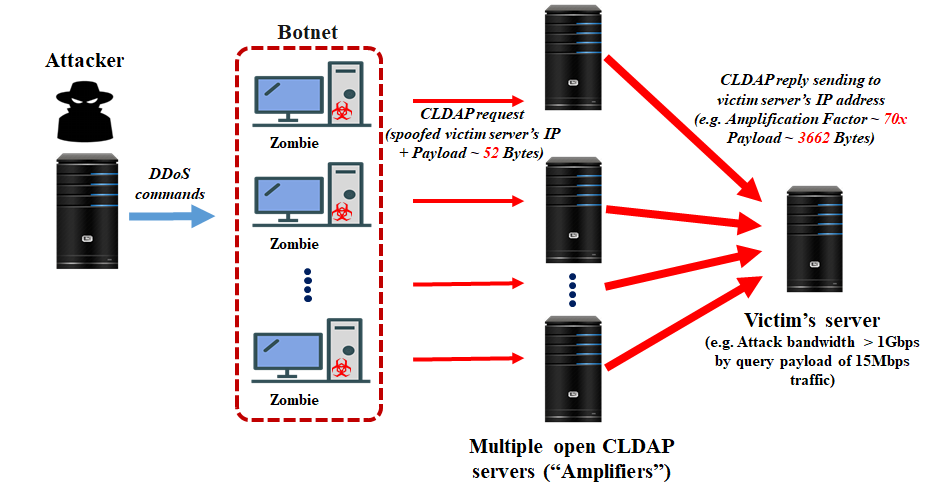
Figure 3: Example of a CLDAP amplification attack
The followings are some best practices for organisations to protect against DDoS attacks.
Organisations should monitor the network traffic and usage of system resources regularly to detect traces of DDoS attacks so that they can take prompt action to contain the damages caused and eradicate the DDoS attacks.
Organisations should contain the damages caused by DDoS attacks before they overwhelm resources and increases the damage caused.
Organisations should evaluate the damages caused by DDoS attacks and draw up suitable recovery measures in order to resume the affected services and prevent the same attacks from compromising the services again in future.
Disclaimer: Users are also recommended to observe the disclaimer of this website and read the user agreements and privacy policies of the security software and tools before downloading and using them.
