Security of DNS
What is Domain Name System (DNS)?
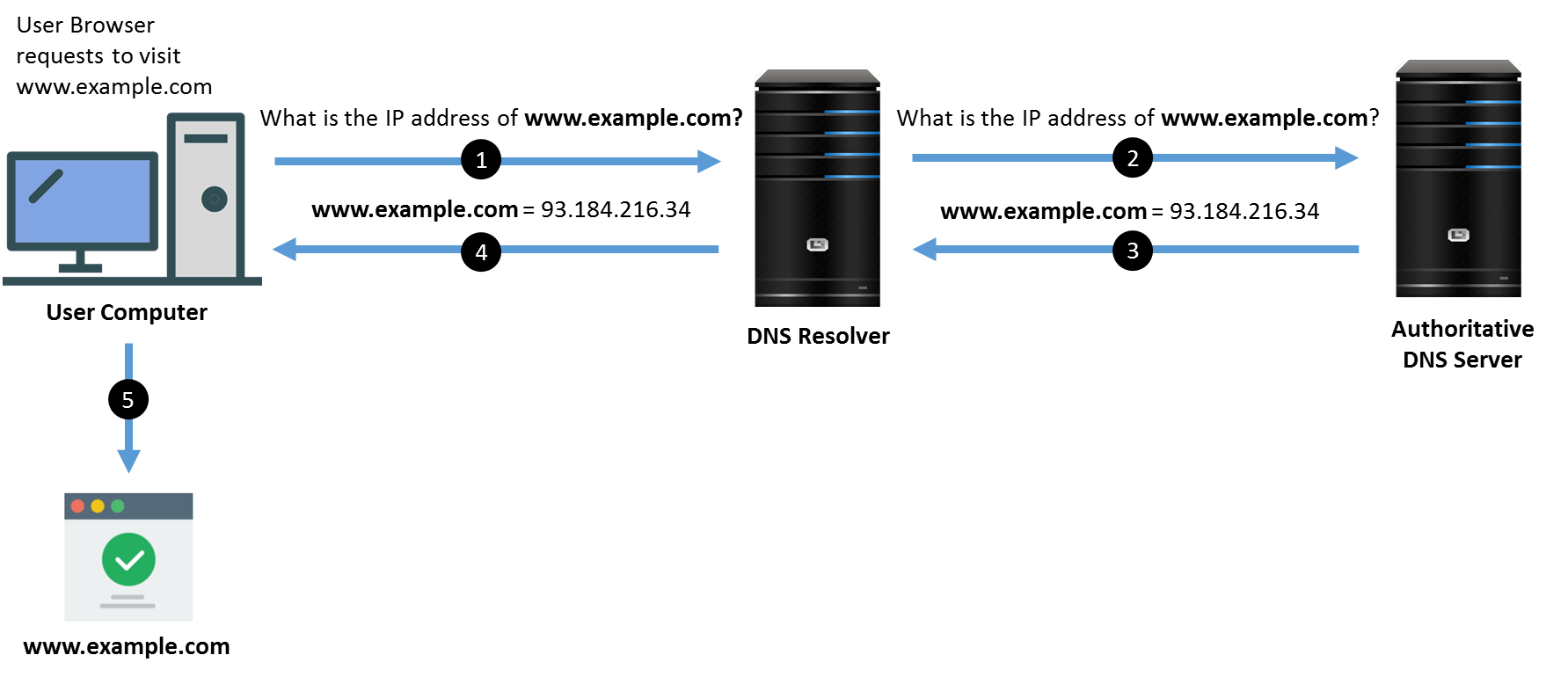
DNS stands for “Domain Name System”. It resolves human-readable Internet domain and host names, such as www.example.com, to machine-readable Internet Protocol (IP) addresses like “93.184.216.34” and vice versa. The Internet is an IP network, and DNS acts like a directory or phone book of the Internet. The following illustrates by an example on how DNS works.
Common Security Risks of DNS
DNS has no built-in security feature and DNS data could be tampered. If the DNS response is tampered, a user might be redirected to a malicious website. If the computer gets infected with malware, the information stored on the computer could be at risk. The following table summarises some common security risks of DNS.
| Security threat | Brief description | Impact on users |
|---|---|---|
| Cache poisoning | Malicious attackers exploit vulnerabilities in DNS servers to inject fraudulent information that can re-route users to a malicious site | Infected by malicious code embedded in the malicious site. May lead to data leakage or be further used to launch cyber attacks |
| Denial of service attack | Malicious attackers generate Internet traffic to overwhelm the target DNS server with the aim to degrade or break down the DNS service | May fail to access Internet services due to the degraded performance or unavailability of the DNS service |
| DNS spoofing | Malicious attackers impersonate a DNS reply with fake information so as to redirect users to a malicious site | Infected by malicious code embedded in the malicious site. May lead to data leakage or be further used to launch cyber attacks |
| Typosquatting | Malicious attackers register a domain name that is almost identical to the targeted one with the aim to misdirect users to a malicious site | Infected by malicious code embedded in the malicious site. May lead to data leakage or be further used to launch cyber attacks |
To protect from falling victim to DNS threats, measures at different levels could be adopted. At the level of Internet service providers, they should consider adopting Domain Name System Security Extensions (DNSSEC), while users could consider adopting secure DNS-resolving service at their end-device.
Domain Name System Security Extensions (DNSSEC)
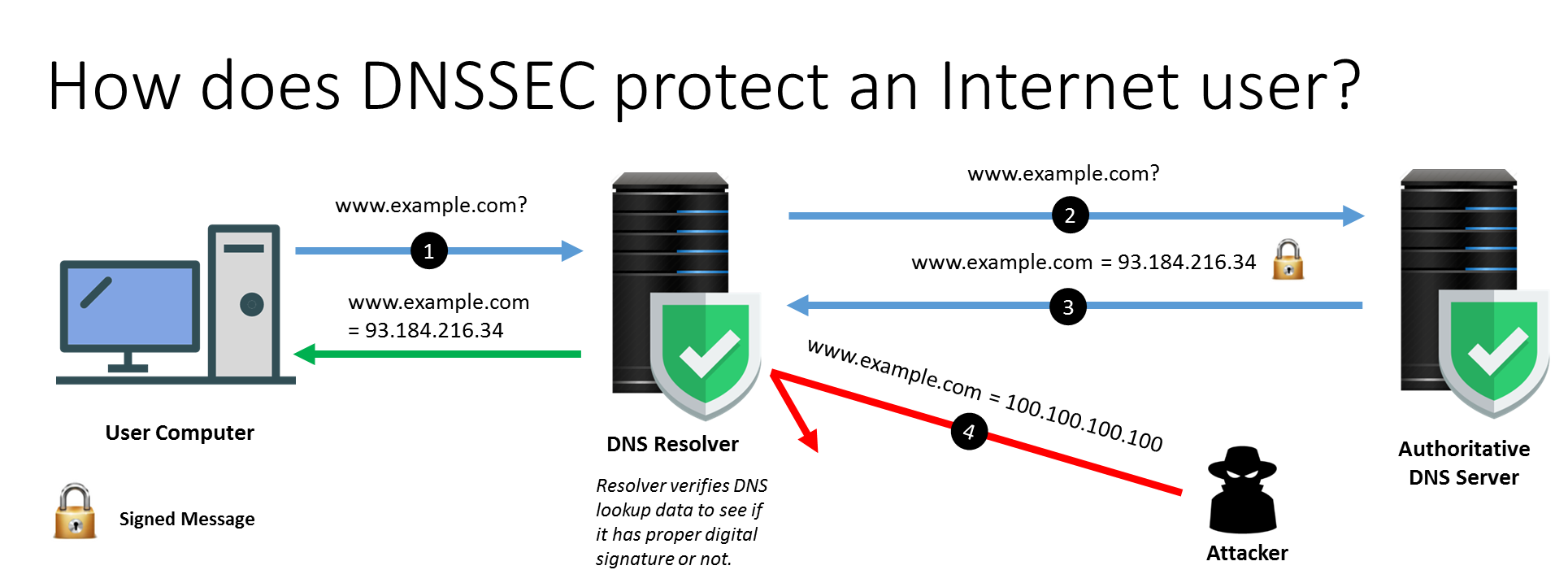
Domain Name System Security Extensions (DNSSEC) enhances the security level by validating DNS data of a domain name during the IP address lookup. It uses cryptographic signatures to confirm the DNS data received is genuine.
DNSSEC helps ensure (i) data integrity and (ii) authenticated origin of DNS data, and thus helps prevent an attacker from redirecting users (at DNS level) to a fake website. However, it should be noted that the domain should be DNSSEC-enabled and the DNS resolver should be DNSSEC-aware in order to provide the protection.
How does DNSSEC protect an Internet user?
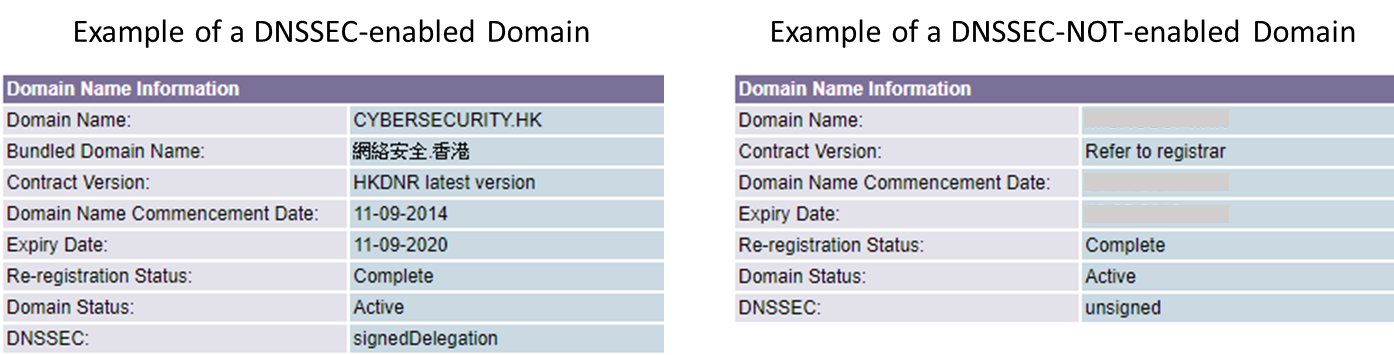
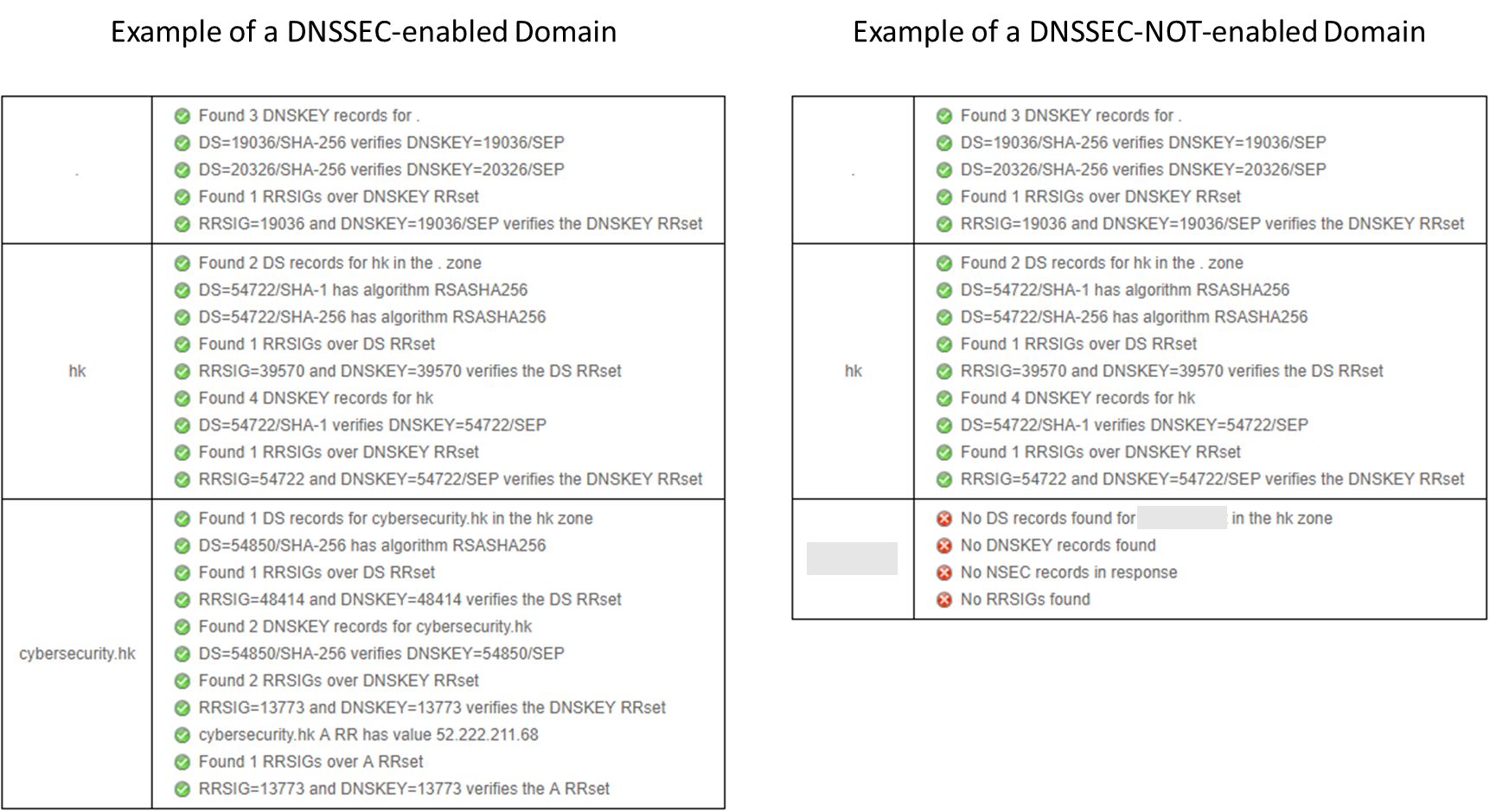
Is a Domain DNSSEC enabled?
You may check whether a domain is DNSSEC-enabled by:
Secure DNS-resolving service
No matter DNSSEC is enabled or not, a user should protect oneself from falling to the trap of malicious attackers by adopting secure DNS-resolving service. The service would automatically review the domain being requested and block those malicious domains.
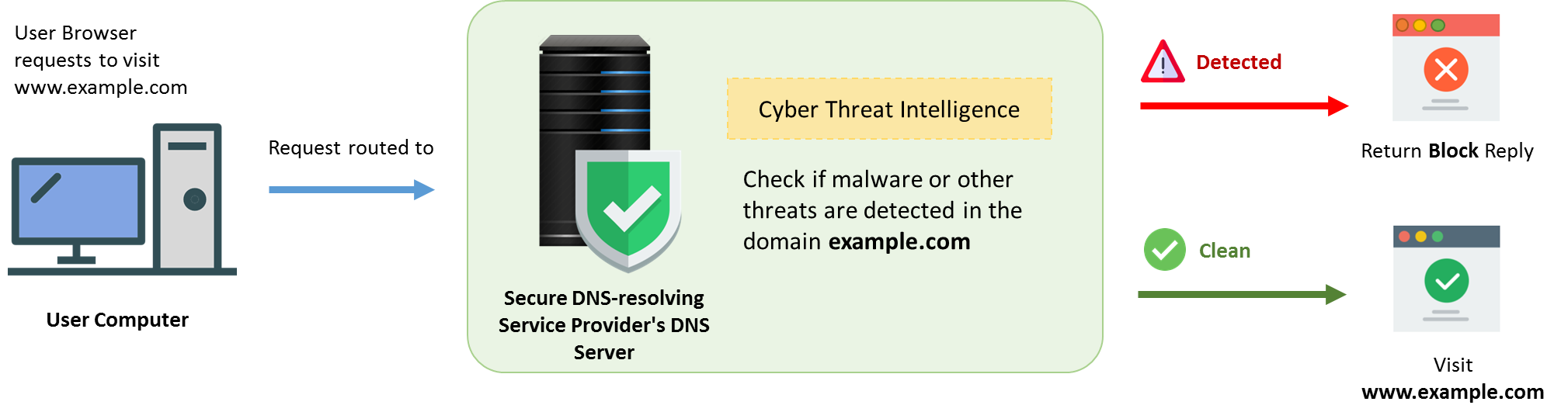
How to adopt secure DNS-resolving service?
There are some secure DNS-resolving services available to home users for free, e.g. Quad9 and OpenDNS.
Quad9
Details on how to configure Quad9 on Windows are available at https://www.quad9.net/#/setup/microsoft
Details on how to configure Quad9 on MacOS are available at https://www.quad9.net/#/setup/apple
OpenDNS
Details on how to configure OpenDNS on different platforms such as home routers, Windows and MacOS, and some smart devices are available at
https://support.opendns.com/hc/en-us/categories/204012907-OpenDNS-Device-Configuration
https://www.cybersecurity.hk/en/expert-2017-09-26-Safeguarding-your-Domain-Name-with-DNSSEC.php
https://www.hkirc.hk/content.jsp?id=297&
https://www.internetsociety.org/deploy360/dnssec/basics/
Disclaimer: Users are also recommended to observe the disclaimer of this website and read the user agreements and privacy policies of the security software and tools before download and use them.